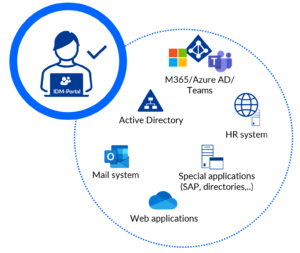
Understanding components of IT compliance
Compliance with laws and internal and external contracts are an important factor for the IT landscape. For IT compliance, the IT infrastructure must meet a number of requirements.
In this post, we’ll address what responsible parties should look out for. At the same time, we show how you can use identity and access management to strengthen IAM compliance in your company.
What does IT Compliance mean
In simple terms, IT compliance describes a binding guideline for adhering to rules and other regulations in the area of IT infrastructure. Within the framework of IT compliance, internal requirements can also be implemented to significantly increase IT security in a company. Examples of this are:
IT compliance in a company ensures that an organization handles all processes in accordance with the law. Contracts that exist in the company and with customers or partners are also part of IT compliance, as the security of data processing is defined here. IT compliance is part of IT governance. This also includes guidelines for controlling, business processes and management.
International conventions, EU directives, “unwritten laws”, “trade customs”, moral obligations in data processing or a wide variety of other rules can be combined to form a central IT compliance in the company. Finally, it is also about a code of conduct. This describes the work of the employees in the company with regard to the:
- handling of the IT infrastructure
- protection of data
- handling of security problems
Helping to achieve this are reliable IT services and applications, such as an identity and access management system that specializes in IAM compliance.
IT helps to ensure compliance
If companies or individual employees do not adhere to the various rules, the entire organization feels the negative effects. For this reason, clear rules and structures are necessary to minimize the risk of compliance violations.
The IT infrastructure is an important tool in this process. IT compliance therefore not only describes adherence to the defined rules while working with IT. Rather, it also ensures compliance with the rules that IT makes possible in the first place.
An example of this is the handling of logon data and personal information. These are much more secure and effective with well-structured IT systems than without an optimally adapted environment for managing user logins. Through connections with HR systems, employee credentials and data can be managed more easily, securely and, most importantly, with firmly defined rules based on IT compliance. IT is not only a component of compliance, it is, properly used, a tool to be able to adhere to IT compliance at all times.
By using an IAM system, such as FirstWare IDM-Portal from FirstAttribute AG, important rules can be enforced that strengthen compliance. In particular, access authorizations are more secure and easier to manage through automated processes.
Focus on IT security for all systems
The compliance requirements for IT consist primarily of
- the security of all IT systems,
- their availability and
- the definition of optimal data retention and archiving.
Data protection also plays an essential role here, since most companies process a great deal of personal data in IT processes.
As part of IT compliance, documentation should take place, from which the potential dangers emerge on the basis of a risk analysis. Hardware and software play just as important a role here as the rest of the IT infrastructure, i.e., including the data center, the building, and the various security systems relevant for access to the data centers.
If companies use cloud services, security and data protection are also very important here. In addition to security, the various licenses are also relevant, because all commercially used products must of course be properly licensed. License violations can cause high costs. Companies should avoid incorrect licensing through IT compliance.
GDPR, IT Security Act, ISO 27001
In addition to contracts and specifications to which companies subject themselves, the General Data Protection Regulation (GDPR) and the IT Security Act (Act on Increasing the Security of Information Technology Systems), which is particularly relevant for operators of critical infrastructures (CRITIS), are important for IT compliance in the EU. These include telecommunications providers or hospitals.
The Act on Control and Transparency in Business (KonTraG) is intended to improve corporate governance, especially in German companies. In addition, the ISO 19600 and ISO 27001 certifications are still a basis for many companies. With ISO 27002:2022, the Information Security Management Standard receives new measures. Those certified to ISO27001:2013 have about two years to complete certification to the new standard.
Using ITIL and COBIT for more IT security and efficiency
With IT frameworks such as ITIL or COBIT, companies can ensure that IT processes run according to standardized specifications and are as secure and efficient as possible. The specifications are not mandatory, but they help to operate the company’s own IT infrastructure as securely as possible, drawing on the experience of the authors. At the same time, adherence to the ITIL and COBIT specifications almost always improves IT compliance.
How to achieve optimal IT compliance in your company
Define requirements for IT compliance
First, it should be documented exactly which laws, standards and contracts play a role for the company that must be observed without fail as part of IT compliance. Then a list of the processes, programs and IT infrastructure affected should be drawn up, which relates to IT compliance. Within this framework, it is already possible to determine which requirements the individual processes must fulfill, especially the processes for the personal processing of data.
There may still be different areas in the company that have different IT compliance requirements. Here, it may also make sense to carry out modernization measures, for example to connect HR systems directly with the systems for managing user accounts.
In order to perform the onboarding of new users more effectively, faster and with fewer errors, a solution with a focus on IAM compliance is ideal, especially if Active Directory is used as the database.
Identification of risks
Part of the development of an IT compliance is the identification and discussion of risks that a company expects if it does not adhere to compliance. In doing so, it is also useful to record impending penalties for responsible persons in the company as well as fines and other negative effects.
Clear communication of processes and regular audits
Once all the requirements are clear and the IT compliance policy has been created by the various people responsible in the company, it must of course be publicized within the company. The binding nature must be just as clear as its enforcement and monitoring. A compliance manager can holistically check compliance and conduct audits at regular intervals. Detected weaknesses can thus be identified and remedied on an ongoing basis, and the associated processes optimized. This should be accompanied by training sessions to bring employees up to date and raise their awareness of the issue.
About FirstAttribute AG
FirstAttribute AG is an independent German cloud service and software company focused on compliance-oriented Identity & Access Management (IAM) for AD and M365/Azure AD.
Learn more about our other products and services at About Us.